I’ve been working with a client on their AutoPilot process for AAD joined devices. One of the issue they were encountering was that printer driver installations would fail without prompting for Administrative credentials.
The ‘Install Driver’ dialogue box would surface, and after clicking ‘install driver’ the process would appear to complete, with the driver being downloaded from the print server across the VPN.
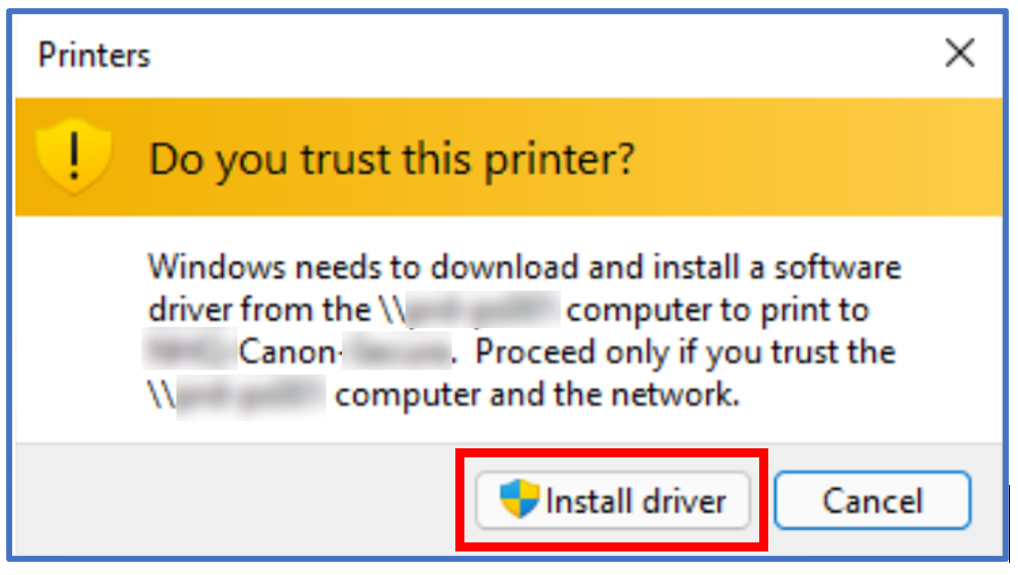
However, once the download had completed, the user was presented with the below message.
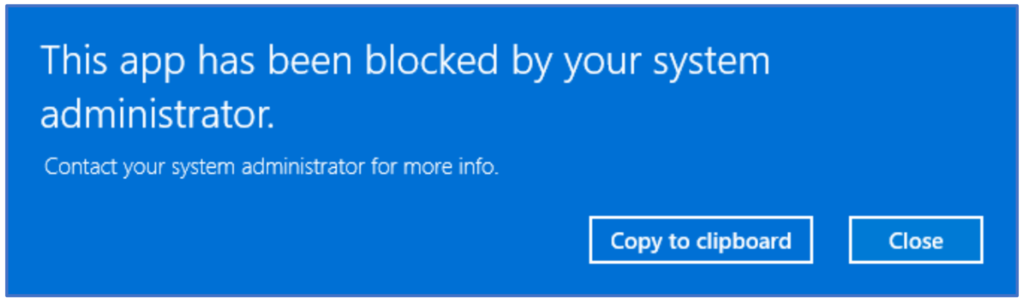
Additionally, the error below was displayed:
Windows cannot connect to the printer. error 0x00000006
This issue was complicated as the devices were configured for shared usage, and had the corresponding shared device policies applied for fast user switching etc.
Historically, managing AAD-joined devices via InTune would quite often require a combination of scripts and registry injections in order to achieve the same results as traditional Group Policy settings. Thankfully, this process has been simplified through the introduction of the Setting Catalog, which allows us to manage devices in a similar way to Group Policy.
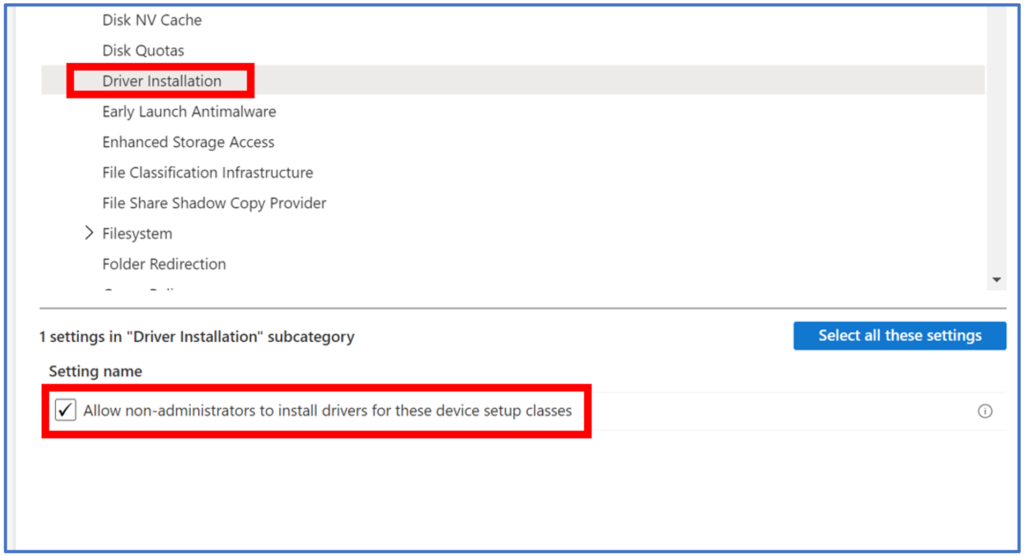
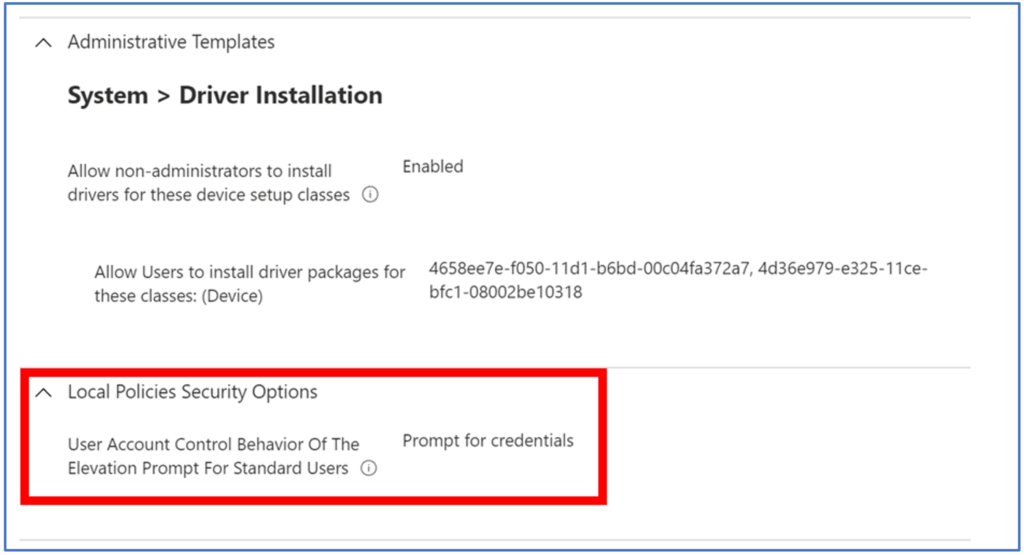
To allow users to install printer specific drivers, we first need to create a Device Configuration Profile using the Setting Catalog. After providing an appropriate name, navigate to System > Driver Installation and enable Allow non-administrators to install drivers for these device setup classes.
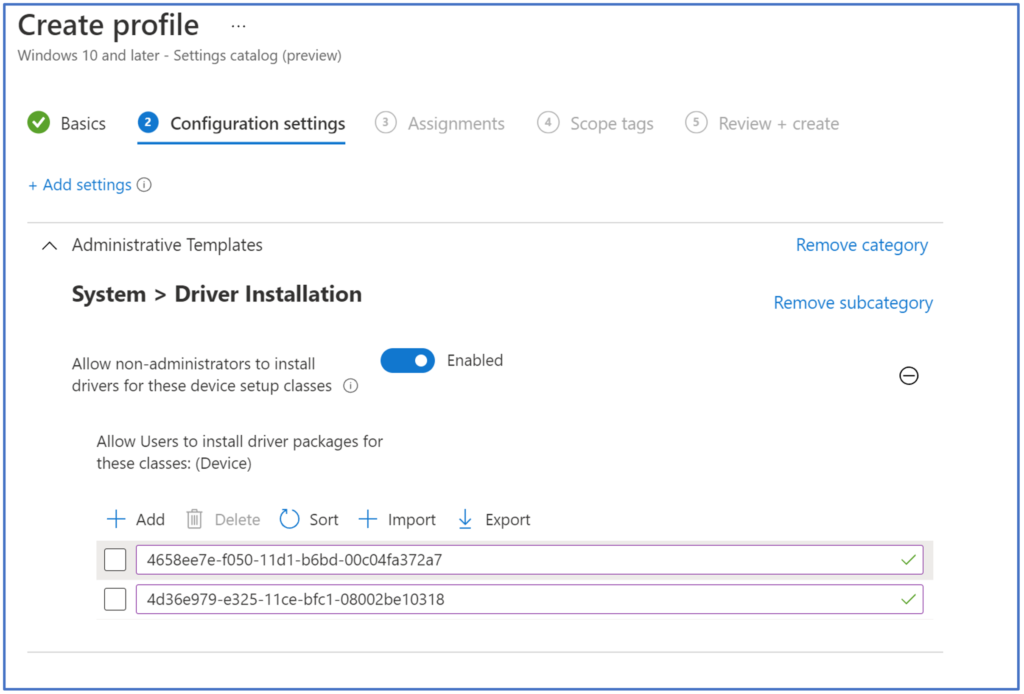
Click next, and then populate the required driver classes. The 2 printer class GUIDs required are 4d36e979-e325-11ce-bfc1-08002be10318 and 4658ee7e-f050-11d1-b6bd-00c04fa372a7, as described in the below article:
The above settings permit the installation of specific device types, but in my case this did not resolve the message ‘this app has been blocked by your system administrator’, this is likely due to the use of shared device policies mentioned earlier.
In order to resolve this issue, I needed to configure another Settings Catalog policy to specify UAC behaviour. Configuring the Local Policies Security Options > User Account Control Behaviour of the Elevation Prompt for Standard Users policy to ‘prompt for credentials’ resolved this issue, and surfaced the expected UAC elevation prompt when installing a printer.
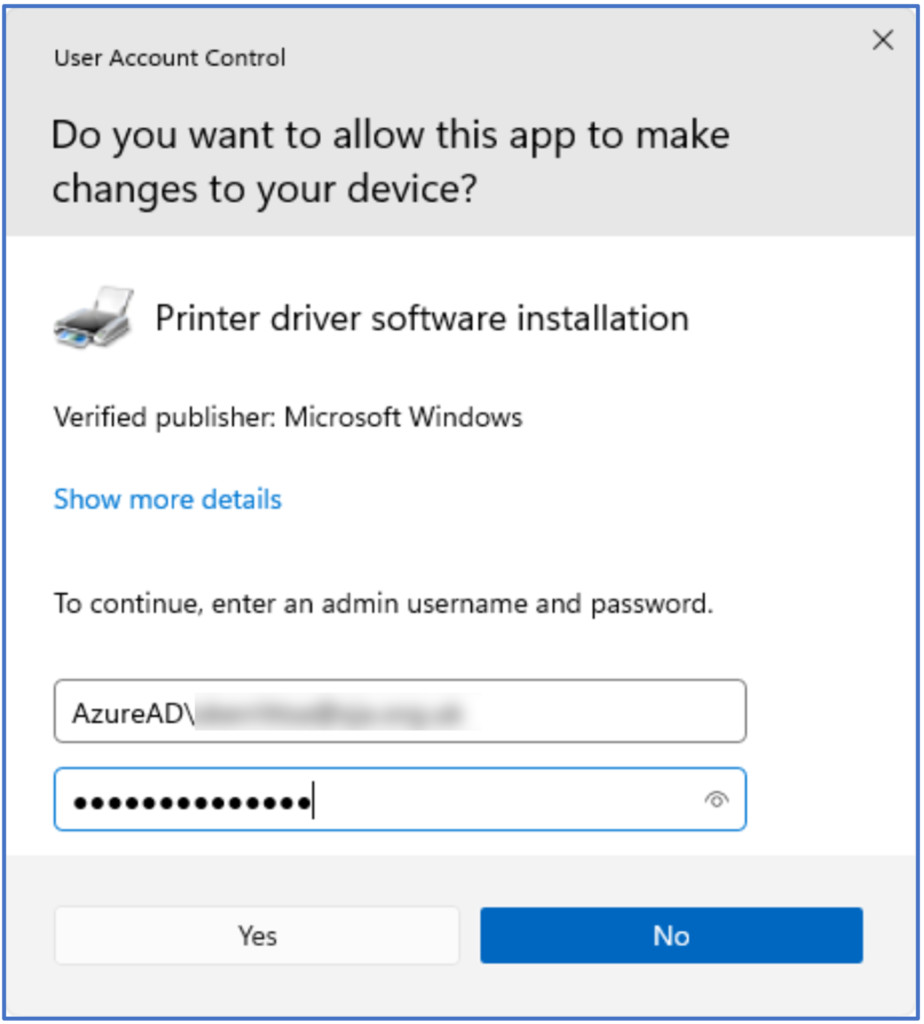
Below: The elevation prompt working as required. Administrative credentials should be formatted as AzureAD\[email protected]
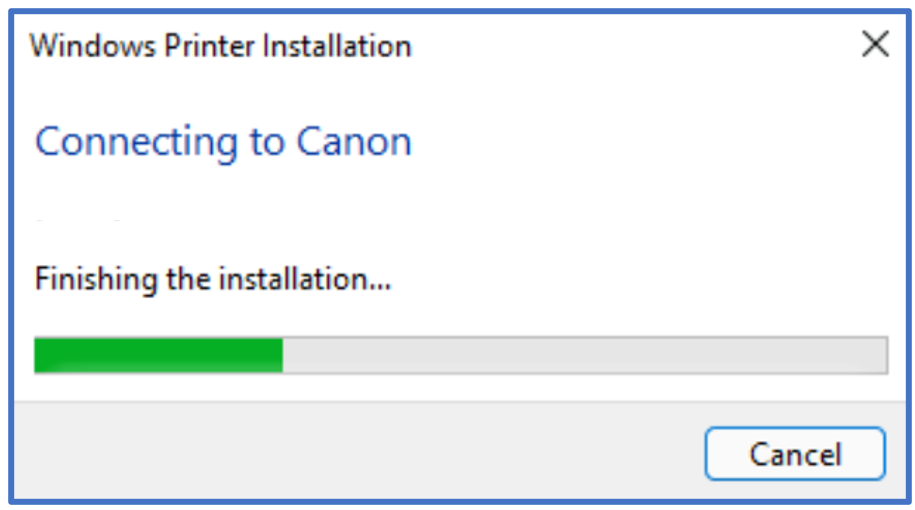
Below: the driver installs successfully.
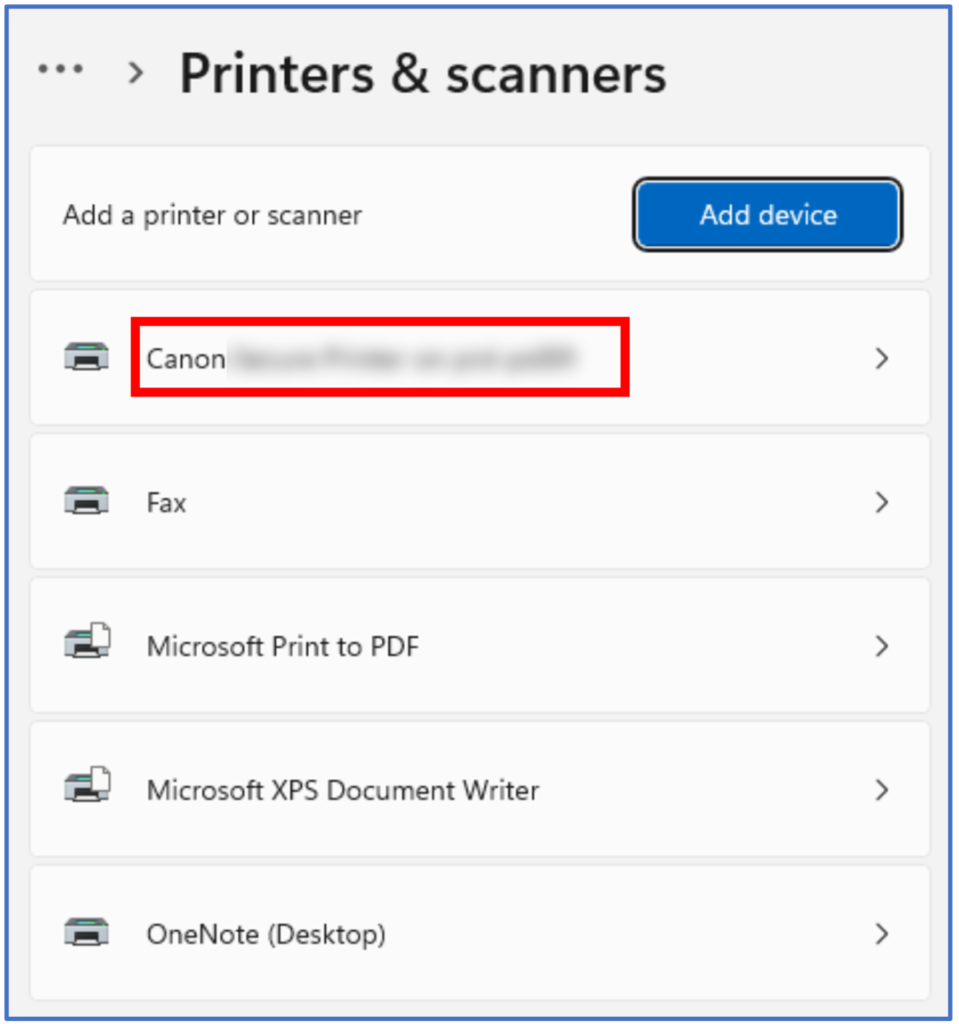
Below: The printer is now available in the Printers & Scanners menu.
Microsoft recommends that network printers should be deployed centrally via policy rather than in the way described above, so this should always be the preferred approach. However, in an age of hybrid working when we may want to allow users to connect to their home printers or when policy may not be appropriate or achievable, this method may provide a handy work around.